
In the event you account for arbitrarily lengthy passwords, the chance of collisions without a doubt increases, but these are definitely just unreachable.
Henrik supports the communityHenrik supports the community 10355 bronze badges $endgroup$ three $begingroup$ It's not at all a good reason for any person to limit the size of passwords.
The central part of any hashing method will be the hashing operate, which normally takes The important thing and converts it to a hard and fast-size string of people. But how just does that work? How could it be that your name and a novel can equally be condensed into the same quantity of people?
Is it acceptable to watch religions as theories, and, If that is so, to look at their theoretical predictions in order to test them empirically?
At time of her Loss of life in August 2022, Heche experienced accomplished filming various films that were nonetheless in write-up-production and where she would appear posthumously.[132] One particular of such films was Girl in Place 13 that aired as part of Lifetime's "Ripped from the Headlines" movie sequence. The Film is about human trafficking and was committed in memory of Heche.
$begingroup$ When applying a dictionary ('I choose to lookup client knowledge by their customer IDs'), The everyday facts constructions used are hash tables and binary research trees.
The first purpose of hashing in cryptography is to deliver a novel and irreversible representation of information. Cryptography makes use of several hash capabilities to protected details.
Hash output. Unlike the input, the hashing course of action's output or hash value contains a check here set length. It is challenging to find out the length in the original enter for the reason that outputs have a established size, which contributes to an In general Enhance in stability.
You are able to set a limit but high sufficient that no realistic person would ever exceed that size. By way of example if I have to enter a password manually, a 10,000 character password would be unachievable to enter in exercise.
Hashish, normally referred to as "hash", is really a cannabis product composed of compressed or purified preparations of stalked resin glands named trichomes.
In the following paragraphs, we will be speaking about of programs of hashing. Database indexing: Hashing is accustomed to index and retrieve data competently in databases together with other information storage programs.
Then, you may additionally set some limit outside of logistical reasons, and that means you need not run the password hash over gigabytes of information whether or not some joker decides to try moving into a password of these types of length.
Double hashing is a collision resolution technique used in hash tables. It works by using two hash capabilities to compute two diverse hash values to get a provided essential.
If a shop prices all things particularly high and applies a "non-legal discount" at checkout, will shoplifters get prosecuted dependant on the high price?
 Jonathan Lipnicki Then & Now!
Jonathan Lipnicki Then & Now! Andrew Keegan Then & Now!
Andrew Keegan Then & Now!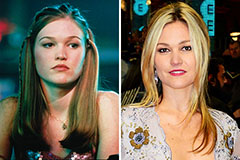 Julia Stiles Then & Now!
Julia Stiles Then & Now! Bill Cosby Then & Now!
Bill Cosby Then & Now! Katey Sagal Then & Now!
Katey Sagal Then & Now!